Yanlin Wang, VP of Advanced Technology, Explains How to Break the Security Mold to Enable Anytime-Anywhere-Anyone Secure Access to Resources Everywhere
This is the first in our secure access blog series — check back weekly to see new articles, or better yet, subscribe to our newsletter and be the first to be notified when new articles are published on our site.
Check out our other blog in this series:
Foreword by Mark Lee, CEO, Co-Founder Splashtop
When we launched our Splashtop remote access and support product line over ten years ago, we were laser-focused on delivering the highest performance and best user experience available for accessing computing resources anywhere. 250K customers and 30M users later, there’s little doubt the market agrees.
As our products matured, our emphasis on security has evolved and expanded into what has become our foundation for the future of remote access, aimed at providing worry-free productivity regardless of location, device, or identity. In working closely with our customers and managed service provider partners, they have expressed the desire for a richer set of access methods to diverse computing devices, and with granular control. Plus, they wanted greater visibility for security and compliance.
Part of our response was our recently announced acquisition of Foxpass, a security platform for secure local (Wi-Fi) and server access. A larger part of our security plans has been less visible, until today.
Two years ago, we kickstarted a security product initiative by recruiting the best and brightest security architects and engineers from leading security firms here in Silicon Valley. Freed from the constraints of siloed thinking and relieved of the baggage of legacy architectures and old code bases, our security team has made rapid progress. We’re finally ready to unveil the foundations of our new security product and extend our early access program to select customers.
More importantly, I’m proud to present our seminal blog introducing the foundations of our security architecture. Authored by Yanlin Wang, our VP of Advanced Technology (and architect of our security platform), it lays down the pillars for the Splashtop Secure Workspace and shows how our more comprehensive approach ushers a new wave of easier-to-use yet more secure remote access solutions.
We’ll be adding to this blog in the coming weeks, showing how common IT access problems can be solved with Secure Workspace, and highlighting a few unique features of the platform. If your curiosity is piqued after reading Yanlin’s blogs, or you feel inspired by our vision, you can express your interest by joining our early access waitlist on the Splashtop Secure Workspace page.
Why Splashtop Secure Workspace?
Splashtop Secure Workspace is a ground-breaking solution that tackles the key issues organizations face in the digital era. It's designed to address modern challenges that come with having a remote workforce, multi-cloud migration, complex network access to resources, and the messy business of managing credentials and secrets – all common headaches for IT teams, big and small.
Today's IT professionals are juggling a whole host of ongoing issues. These range from the laborious tasks of user provisioning, de-provisioning, and onboarding, to dealing with the intricacies of multiple solutions that don’t necessarily play together. Adding to this are stringent compliance requirements, the need to safeguard resources from leaks and attacks, and the vital need for more comprehensive visibility. Then there’s the budgetary challenge of procuring and managing multiple disparate yet overlapping access and security tools.
All these are compounded by the ever-evolving landscape of cybersecurity threats, complicated by geopolitical uncertainties and the rise of organized cybercrime syndicates. It’s clear why IT leaders are plagued by sleepless nights.
To overcome these hurdles, our team at Splashtop has taken a fresh look at the secure access conundrum from a user perspective, taking both end-users and IT administrators into account. Our design philosophy goes beyond merely fitting into outdated, rigid, and irrelevant security or access paradigms established years ago, focusing instead on solving real-life business use cases.
The goal of our architecture, which we’ll delve into below, is to provide a comprehensive and secure environment for employees, contractors and partners to work from anywhere, ensuring seamless access to private and public resources and services.
The State of Remote Access Today
The difficulties experienced in access management can be traced back to a simple root cause. Many organizations rely on a patchwork of disconnected point solutions to address their access needs. This mix includes identity management, remote management and access systems, VPNs, firewalls, and secret vaults – all loosely integrated. This approach gives rise to several challenges and amplifies the frustration associated with access management.
Fragmentation Breeds Complexity and Insecurity
A major culprit behind the current state of the access market today is the lack of integration and cohesion among these disparate components. Each solution operates independently, with limited visibility into the complete access context. For instance, the remote access tool may not have full knowledge of user entitlements stored in the identity management system, or the device and network security posture overseen by endpoint management systems. This fragmented approach leads to a lack of comprehensive understanding and control over access requests.
Moreover, the disconnected nature of these point solutions hinders seamless user experiences. Users often encounter multiple login prompts, tedious authentication steps, and confusion over their access rights and available resources. This results in a suboptimal user experience that hampers productivity and satisfaction.
The siloed nature of these point solutions also leads to incomplete security measures. Each component acts alone, complicating the enforcement of consistent security policies and the implementation of robust security controls across the entire access landscape. This exposes organizations to security vulnerabilities and compliance risks.
Juggling Separate Solutions Creates Headaches
Adding to these challenges, the manual tasks associated with managing a multitude of tools create unnecessary complexity for IT administrators. Their days become burdened with the need to juggle multiple tools, perform repetitive tasks, and manually integrate workflows to meet access needs. This manual effort is time-consuming, error-prone, and inefficient. For small and midsized businesses with lean IT teams, this puts an additional strain on resources.
To overcome these hurdles and modernize access management for the digital era, a greenfield approach is required. Organizations need to transition from a legacy "best-of-breed" approach built around isolated technologies to an integrated and unified solution. The ideal solution should provide seamless integration, comprehensive visibility, and centralized control over access management, ensuring both security and user experience are prioritized.
The Future of Remote Access: Splashtop's Silo-Free Architecture
Splashtop Secure Workspace takes a comprehensive approach to tackle the tough issues tied to access management. Our architecture carefully considers the multiple factors at play in providing access. When a user successfully connects, it signifies that they possess the correct identity, entitlements, device compliance, networking, and validated credentials for the target resource or service. These elements are interconnected and form the foundation of Splashtop Secure Workspace's unified access management system.
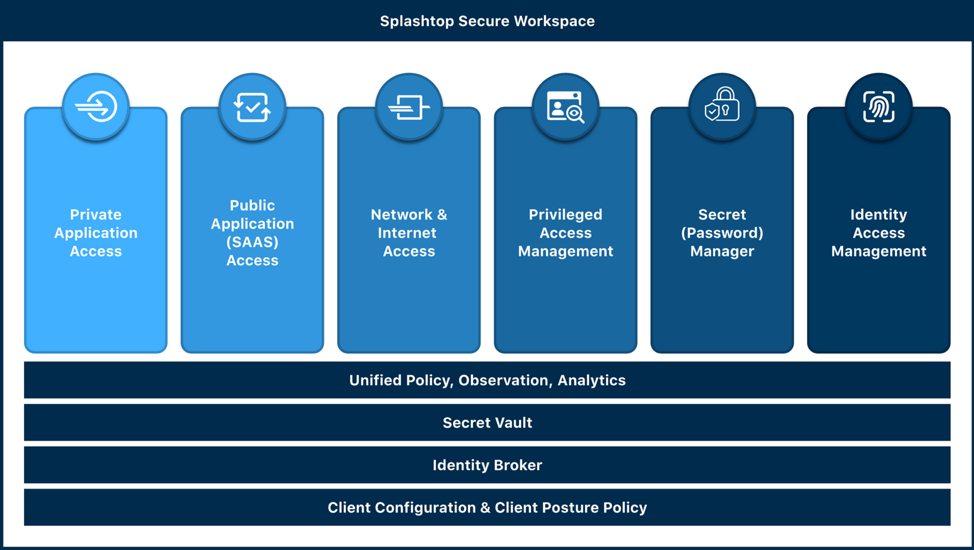
The above is a depiction of the components that make up Splashtop’s Holistic Architecture. Over the coming weeks, we will explain in more detail how these components work together to enable seamless and convenient secure access.
The Splashtop Secure Workspace architecture ensures these foundational layers—identity, device, networking, and secrets—are interconnected. This cohesion allows for a full and contextual understanding of access requests in any given scenario.
For instance, when a user requests access, the system can evaluate their identity and permissions stored in the identity management system, device security status managed by the endpoint management system, and network security posture. This in-depth understanding of the access context paves the way for more effective and secure access control decisions.
The interconnected nature of Splashtop's Holistic Architecture comes with a host of benefits, thanks to this. It creates an environment that enhances user experiences, delivering exceptional performance and continuous access for employees, regardless of their location. Users can enjoy rich and high-quality experiences throughout their work journey.
Moreover, the architecture empowers organizations to enforce robust security measures, including end-to-end Zero Trust principles and conditional access controls. This facilitates seamless and secure access to all applications, whether they reside on-premise, in the cloud, or are SaaS-based.
As a result, organizations benefit from a comprehensive and highly effective security framework that empowers users to access any application from any device with confidence.
Stay Tuned for Splashtop Secure Workspace Real-life Applications
That wraps up our first blog post introducing our new approach to secure access. My next post will unpack how this architecture solves common pain points and access challenges. Stay tuned for that!
Until then, check out our Splashtop Secure Workspace page and join our early-access waitlist.
Check out our newer blogs in this series: Transforming Secure Access: Real-World Applications of Splashtop Secure Workspace and The Splashtop Secure Workspace Admin Experience.


