This is the third article in our secure access blog series. If you haven’t yet, read Yanlin’s introductory piece explaining the foundation and vision for our secure workspace: Transforming Secure Access with Splashtop Secure Workspace, and his article on real-world applications: Transforming Secure Access: Real-World Applications of Splashtop Secure Workspace
Digging Deeper with Splashtop Secure Workspace
I laid out Splashtop Secure Workspace’s holistic architecture in prior articles and showed how our product solves challenging real-world problems. This third article in our series takes a closer look at select features that enable us to address the use cases laid out in my prior article, Transforming Secure Access: Real-World Applications of Splashtop Secure Workspace.
Refresher: Splashtop Security Workspace Product Architecture
Let's dive back into the heart of our product architecture, which was previously illustrated in my initial article, Transforming Secure Access with Splashtop Secure Workspace.
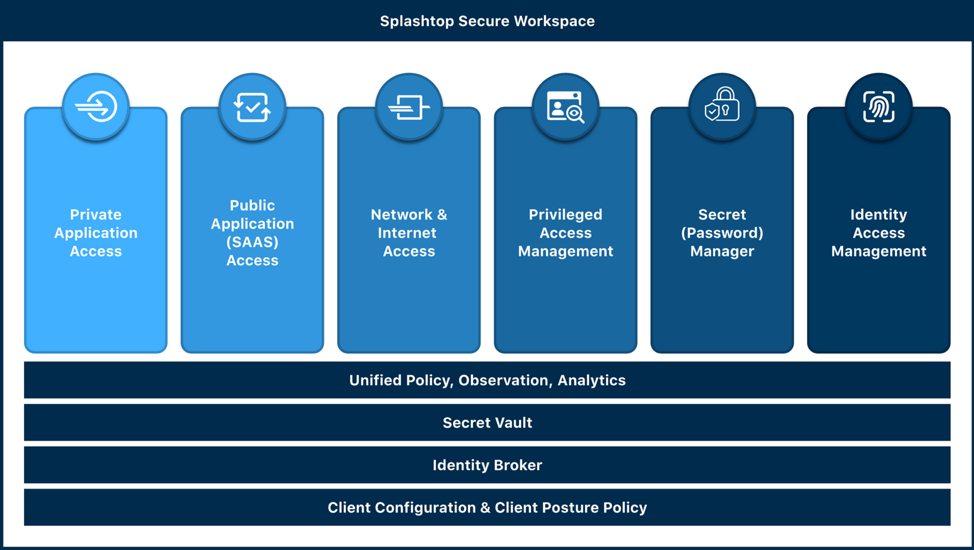
Our architecture breaks free from the traditional “point solution” approach you may see elsewhere in the market. Instead, we've woven a rich tapestry that integrates elements such as identity and credential management, privileged access management, and network and application access controls.
Foundational to our system is an identity-first approach to security, buttressed by integrations with familiar identity providers like Microsoft Entra ID (Azure AD), Google Workspace, and Okta. Our built-in identity broker capability also accommodates others through SAML or OIDC. Splashtop Secure Workspace supports organizations that do not use an external identity provider by providing a built-in user and group manager as an option.
We've introduced a zero-knowledge secrets vault, which forms the bedrock for our password manager and privileged access management frontends. This vault is designed to aid both individual and organizational credential management, and facilitate sharing of secrets like passwords, API keys, and even one-time tokens. The beauty of our zero-knowledge design is that you and you alone (not Splashtop or system administrators) can access the secrets in your vault, ensuring maximum privacy. On-demand decryption occurs directly on your device (desktop, mobile apps, browser) when needed, and shared secrets are only decrypted at the point of use. This protects the integrity of your credentials and minimizes the risk of exposure.
Our platform stands ready to manage access control in three distinct arenas: public Internet-based applications (SaaS), private applications situated both on-prem and in the cloud, and general network/Internet access. We aim to expand the depth and breadth of support over time.
To offer a clear view and easy troubleshooting, we’ve built a state-of-the-art observation system, which we’ll discuss in the next session; Of course, there's much more under the hood than what we can share in a single blog post. If the features outlined here have piqued your interest, we warmly invite you to sign up for early access to our Splashtop Secure Workspace.
Policies — The Engine Behind Secure Workspace
Our journey begins with a core pillar of our system — policies. These create the blueprints that power our Secure Workspace. The diagram below illustrates how the Secure Workspace system (consisting of the Cloud Controller, Web Portals, and our Global Edge Network) gates access from clients to corporate applications and resources.
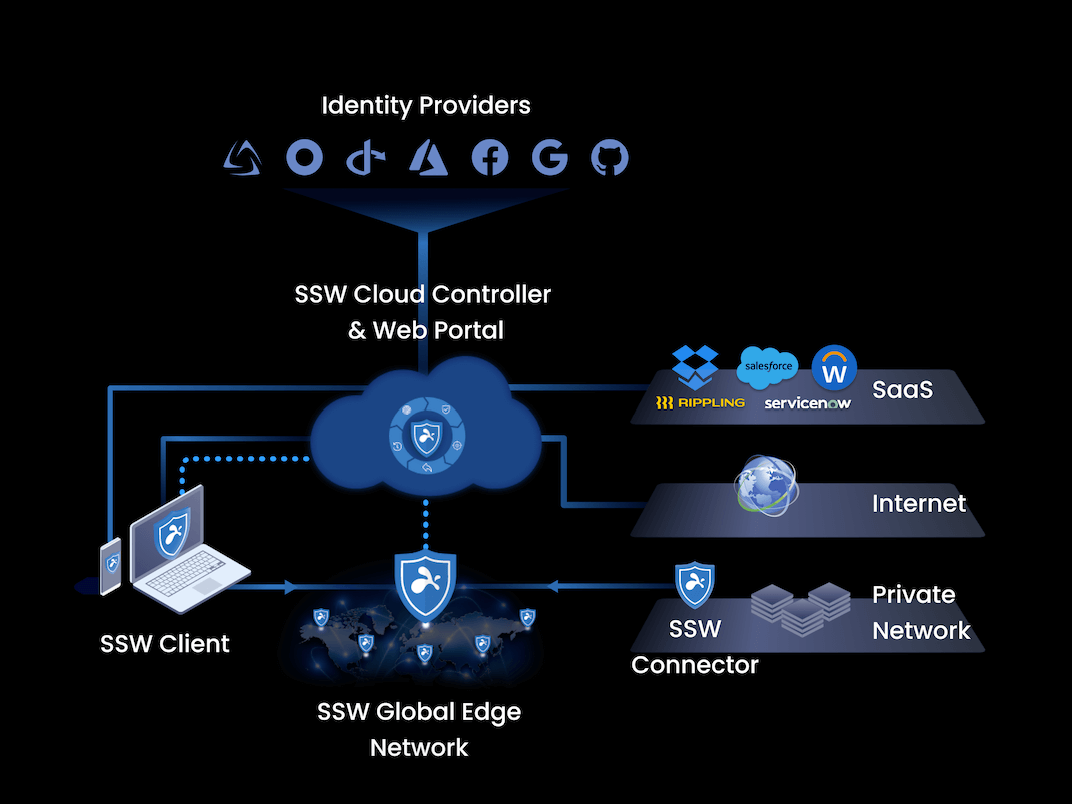
The role of policies is crucial. In addition to the access entitlement setup, they add an additional dimension to the decision of whether access is permissible and under what conditions. Seasoned IT administrators, who have configured remote access products, understand the power of these products is derived from comprehensive policies. Yet, there's an art to balancing the granularity and expressibility of these policies against the simplicity and ease of configuration. We have designed our platform to strike the right balance for you.
One of the keys to making policies streamlined and manageable lies in adopting system-wide policies instead of getting entangled in countless domain-specific policies. Now, I’d like to delve into two such system-wide policies under our system: unified policies and device policies.
Unified Policies at an Organizational Level
Many organizations strive for a consistent security standard guided by either industry best practices or regulatory compliance. Today, IT administrators often find themselves in a juggling act, trying to implement uniform policies across different schemas and security object models.
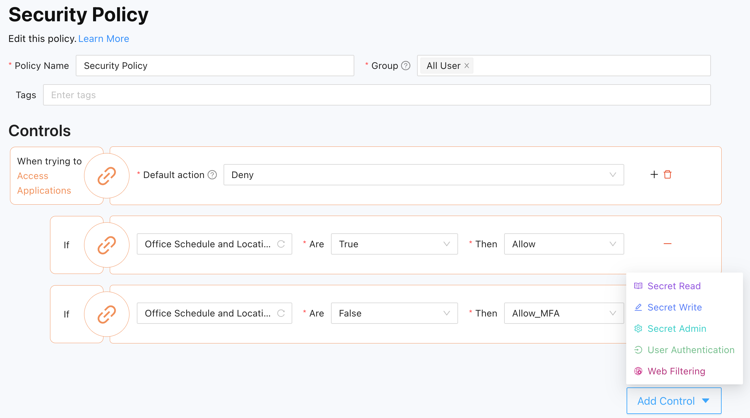
With Splashtop Secure Workspace, we've made it simple for IT administrators to establish a single unified policy system at the organizational level. As you can see, these policies cover a range of elements, from authentication and authorization to application access conditions, secret access conditions, and even web filtering. By implementing these policies in one consolidated place, organizations can uphold standardized access management practices throughout the entire organization.
Device Enrollment and Security Posture Policies
Similarly, we believe in maintaining a uniform security standard across all corporate devices. Splashtop Secure Workspace offers a straightforward way of ensuring each device meets the appropriate level of security before access is granted. With a rich set of controls examining aspects such as disk encryption settings, firewall configuration, anti-virus software presence, operating system versions, and other system attributes, IT administrators can implement the right safeguards to minimize the risk of compromised devices.
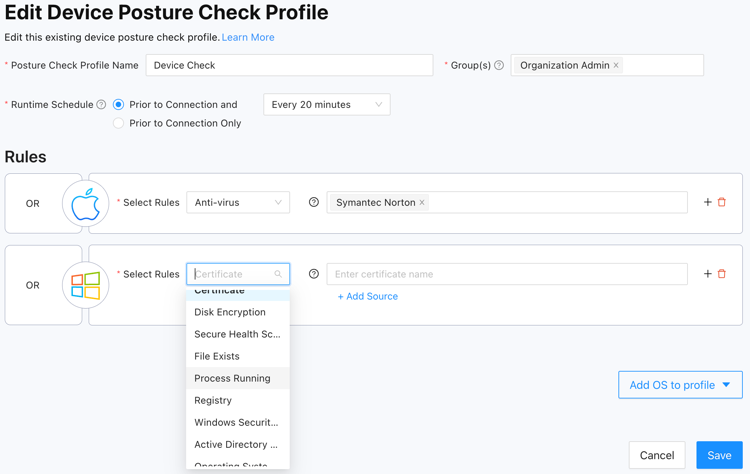
Splashtop Secure Workspace also controls the enrollment of devices onto the system, allowing for IT-in-the-loop approvals as necessary to confirm device identity. Every access attempt undergoes thorough certificate-based checks to validate the identity of these devices.
Application and Secrets-Level Access Policies
With foundational policies securely in place via unified and device policies, IT administrators can go a step further by defining conditional access policies at the application and secret levels.
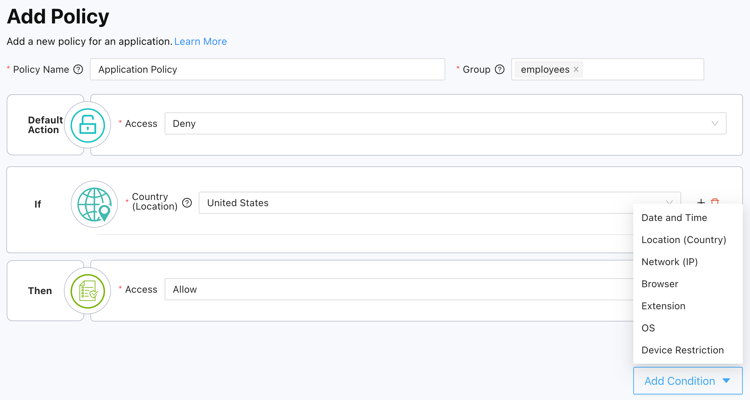

These granular policies consider a variety of factors, such as time, location, device, network, browser, and operating system, giving IT administrators unparalleled precision and control over who can access applications and secrets. The more carefully IT administrators fine-tune conditional access rules, the greater their ability to build flexibility and enhanced security into the organization’s access management processes.
Setting the Stage for Application Configuration
Earlier, we discussed policies for access to applications, which represent the resources we aim to secure. Let's now turn our focus to the configuration of these applications.
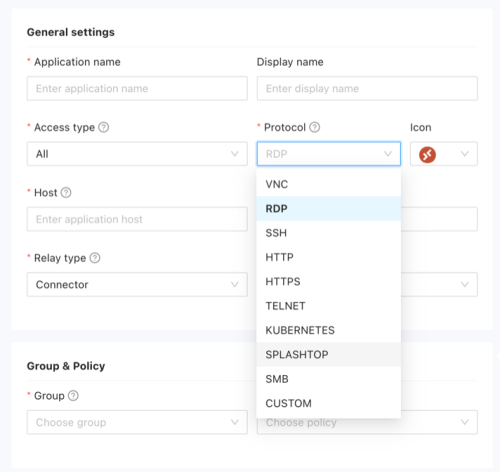
Our platform can gate access to an array of application types. Categories of applications include private or public SaaS applications, RDP or VNC access to Windows, Mac, or Linux devices, file shares (Microsoft SMB), or even a video stream from a surveillance camera stationed in your office or retail outlet. With Secure Workspace – for select protocols such as RDP, VNC, telnet, SSH, and Kubernetes control – we can provide both client access and client-less browser-based access from any popular HTML5 compatible browser.
In Secure Workspace, public applications refer to SaaS solutions that provide access through Single Sign-On (SSO) mechanisms such as SAML and OIDC. On the other hand, private applications may run on the internet or a private network and typically do not support standard SSO integration. For applications hosted on a private network, Splashtop Secure Workspace Connectors enable seamless access. These connectors are installed within the private networks hosting the applications, be it in remote offices, company campuses, private data centers, or even virtual private clouds within public clouds, such as Google, AWS, and Microsoft Azure. Here’s a snapshot of the diverse deployment options available for our connectors:
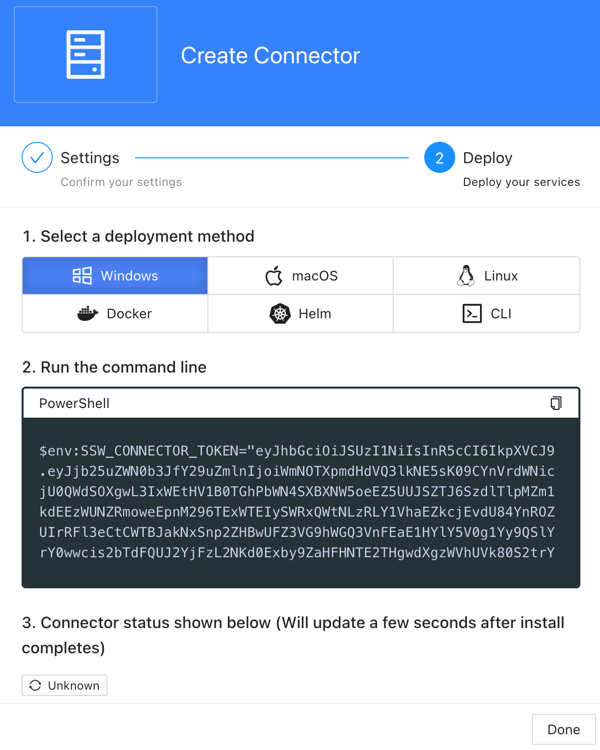
The conditional access policies discussed in the previous section govern access to these configured applications. Moreover, our built-in secrets vault facilitates the assignment of shared secrets for application access. This feature allows both employees and external parties to access applications without needing to remember login details or know the passwords.
Once applications are configured, they appear in the Secure Workspace web portal, browser extensions, and desktop and mobile applications allowing for “one-click” secure access to the assigned applications based on the user's group membership within the organization.
Unveiling Secure and Convenient Access Sharing
Let's move on to a use case I've touched on before: seamless and secure third-party access. Thanks to the integrated secrets vault, privileged access management features, and public and private access methods, Splashtop Secure Workspace enables seamless application sharing for both employees and third parties.
Here's a glimpse at what application sharing configuration looks like for third-party access:
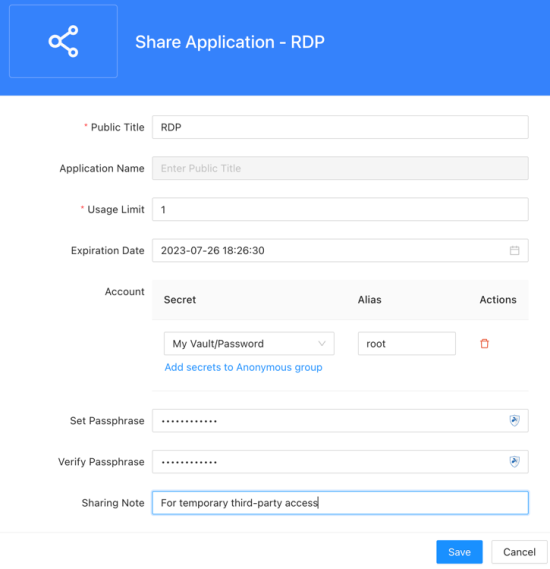
To visualize this in action, look at this brief video:

The video demonstrates how Splashtop Secure Workspace enables the ad-hoc sharing of access with third parties using a temporary access link. In addition, the platform gives IT the power to rapidly onboard third parties that have longer engagements with the organization – such as contractors, interns, and auditors – by leveraging Identity Providers (IDPs). It also enables the use of dynamic credentials that allow the sharing of private application access (via a passphrase, for example) without revealing the actual credentials.
It resolves an ongoing pain point that IT administrators have failed to address, even after trying to combine multiple products.
Constant Vigilance: Key to Security
An essential aspect of any secure access platform is the ability to monitor and log all events. Splashtop Secure Workspace equips IT administrators with real-time session management tools. This allows them to oversee active user sessions, terminate them if necessary, and enforce session recording for auditing and compliance. This real-time visibility and control over sessions enhances security and boosts efficient session management.
In addition, our platform offers comprehensive visibility through event logs and session video recordings. By harnessing rich telemetry data, organizations can gain insights into a wide array of events and review session recordings as needed. This comprehensive visibility fortifies the security posture of the entire organization.
Experience It For Yourself
While we have discussed the key aspects of Splashtop Secure Workspace, there are many more features I am excited to share with you. The best way to truly experience the full potential of the platform is to sign up for early access.
While waiting to get access, feel free to explore the Secure Workspace documentation and other learning resources at your disposal.
In my upcoming blog post, I'll demonstrate a practical, real-world application of how Splashtop Secure Workspace can control access to your private large language model (LLM)—indeed, your own personal "ChatGPT" that will not accidentally leak your data. Stay tuned!


