Delighting and Protecting Our Customers: Thoughts From Mark
On March 19, 2021, computer giant Acer reported that it had been hit with a record-breaking ransomware demand of $50 million. While the ransom amount was staggering, the mere fact of a company being hit by ransomware has become common news these days.
Companies large and small have been victims of ransomware, in which cybercriminals use malicious software to prevent a company from accessing its data, computers, or network unless they pay a hefty ransom fee.
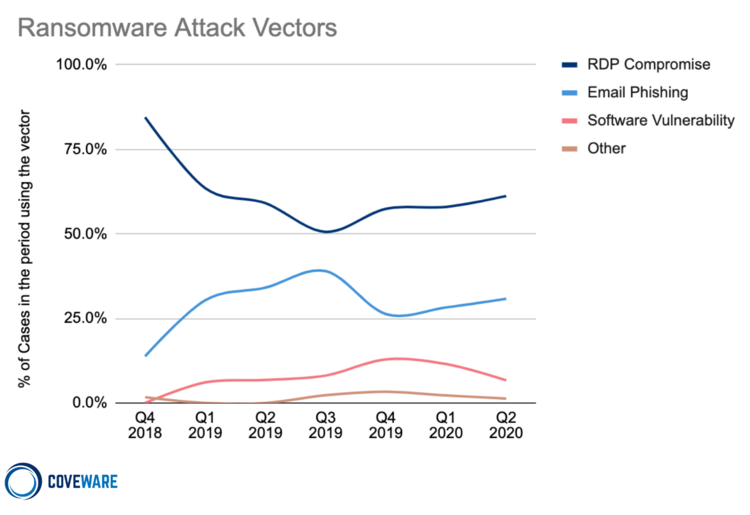
As the CEO of a remote access and remote support solution provider, I’m especially aware of regularly reported ties among virtual private networks (VPNs), Remote Desktop Protocol (RDP), and ransomware. The top exploits used by ransomware gangs are VPN bugs, but RDP still reigns supreme: As outlined in a ZDNet article, reports from Coveware, Emsisoft, and Recorded Future “clearly put RDP as the most popular intrusion vector and the source of most ransomware incidents in 2020.”
Concerns about ransomware have grown during the COVID-19 pandemic, with so many employees working from home. Global accounting firm KPMG reported evidence that “remote working increases the risk of a successful ransomware attack significantly... due to a combination of weaker controls on home IT and a higher likelihood of users clicking on COVID-19 themed ransomware lure emails given levels of anxiety.”
In June 2020 the Department of Homeland Security issued a warning about a rise in ransomware targeting businesses relying on RDP and VPN for remote access.
Fortunately for Splashtop customers, Splashtop is designed with a zero trust security framework in mind, the latest industry-standard approach that means trust nothing and verify everything. We believe that zero trust can help stem the tide of ransomware attacks.
How Splashtop Helps Prevent Ransomware
While cyber threats are evolving every day, here are some of the ways that Splashtop products help reduce ransomware:
Automate security updates and patches — Today’s VPNs and RDPs all require manual patching, and because VPNs are running 24/7, IT professionals and MSPs are less likely to keep them updated. All it takes is a moment of inattention for a hacker to exploit a vulnerability. Splashtop automates updates for all our end points and cloud infrastructure.
Support device authentication — Unlike most VPNs, which are rarely configured to support device authentication, Splashtop is automatically configured to authenticate any new device trying to establish a remote access session. IT teams can also prevent remote access users from adding new devices.
Enforce multi-factor authentication (MFA) and Single Sign-On (SSO) — Identity verification is a core part of the zero trust framework, and Splashtop supports MFA as well as SSO. Our Splashtop Enterprise product offers SSO/SAML (security assertion markup language) integration with Active Directory (AD), Active Directory Federation Services (ADFS), Okta, and other directory services. Through directory services, IT/MSPs can also enforce password policies such as password strength and password rotation.
Provide session recordings and session logs — Splashtop offers extensive session logs and recording features. As desired, Splashtop Enterprise also integrates with Security Information and Event Management (SIEM) for centralized logging.
Offer endpoint security — Splashtop partners with Bitdefender and Webroot to offer enhanced endpoint security capabilities for customers who want an extra layer of protection.
Ever since the pandemic began, many business turned to VPN and RDP to enable remote work, exposing their businesses to expanding cyber threats. In recent years, Gartner and many security experts have recommended that businesses move away from network-level VPN access and instead move toward application-level, identity-based remote access solutions that embrace a zero trust framework.
Splashtop’s cloud-first, cloud-native secure remote access solution has been designed to support the post-COVID work-from-anywhere era.
Splashtop continually monitors the latest cyber threats, and we are committed to investing millions to ensure our customers are well protected against them. Recently, we have formed a Security Advisory Council and launched a Security Bulletin to help IT pros and MSPs stay on top of latest vulnerabilities.
Find out more about Splashtop remote access security practices. And let’s keep working on ways to make ransomware as rare as possible.