Cybersecurity agencies across the globe are warning organizations about the increased threat of cyberattacks. Learn how to protect your organization.
Across the globe, cybersecurity agencies are warning private and public sector organizations about the increased threat of ransomware attacks and other targeted attacks originating from the crisis in Ukraine. The U.K.’s National Cyber Security Centre (NCSC-UK) calls out ransomware as the most prevalent threat, particularly for the education industry.
In response to the Russia-Ukraine War, Australia, the U.K. and the U.S. issued a joint advisory that highlights the heightened globalized threat of ransomware attacks on critical infrastructure organizations. In addition, The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) in the U.S., as well as the U.K.’s National Cyber Security Centre (NCSC-UK) have called out multiple industries, including education, financial services and healthcare.
The agencies have highlighted initial access to networks via phishing attacks to steal credentials as well as remote desktop protocol credential theft and brute force attacks to guess at credentials.
What makes the Russia-Ukraine War the focal point is that Russian hackers have been at the center of some of the largest and most notorious cyberattacks in recent years, including the SolarWinds attack that impacted multiple government agencies in 2020. In fact, U.S. agencies issued a Russia-specific warning to executives at major U.S. banks just two weeks ago. Following recent developments around Ukraine, Reuters reports that the U.K.’s NCSC instructed U.K. organizations to "bolster their online defenses."
Is your organization really at risk?
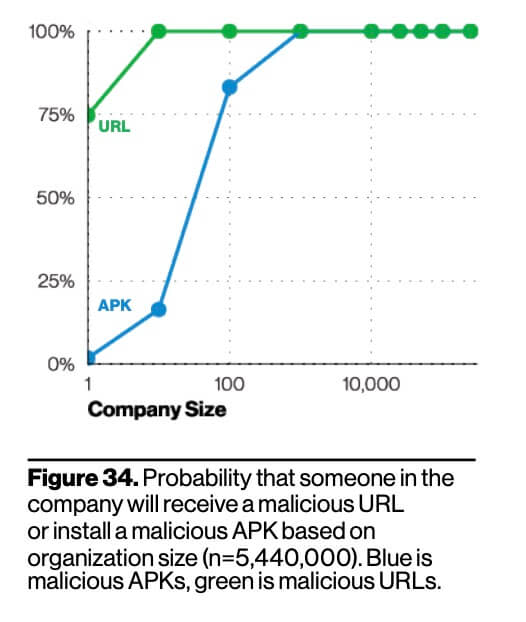
Many U.S. and European organizations (especially small and midsize businesses) ignored or did little to prepare based on past warnings. The Verizon 2021 Data Breach Investigations Report proves that there is a 100% chance that your organization’s employees will be targeted by a cyberattack if your organization has 100 or more employees.
Your risk is even greater if somewhere in your supply chain or business partnerships (even partners of your partners) there exists a Ukraine-associated organization. On February 22, 2022, analysts at S&P Global Ratings flagged "a heightened risk of cyberattacks on Ukraine...which could create knock-on effects for corporations, governments, and other parties in the region and beyond." The analysts pointed out that companies around the world with “connections to Ukrainian systems might be used as a pivot point to other targets,” according to CNN.
Just last week, the cybersecurity firm ESET tweeted out their discovery of new “wiper” malware targeted at Ukrainian organizations. Wiper attempts to erase data from any system it compromises.

Source: @ESETresearch
Your insurance may cover cyberattacks, but will it cover “acts of war”?
When the NotPetya malware infected computers worldwide in 2017, it began by infecting Ukrainian organizations and then spread rapidly. Soon, Maersk A/S of Denmark, Merck of the U.S. and WPP PLC of the U.K. were all impacted. Overall, the attacks caused nearly $10 billion in damages and were attributed to GRU, the main Intelligence Directorate of Russia’s Armed Forces.
One of the most consequential (and as-yet-unresolved) legacies of NotPetya centers on Mondelez International. Mondelez is a multinational food company headquartered in Chicago that makes Oreos and Triscuits, among other beloved snack foods. NotPetya infected the computer systems of Mondelez, disrupting the company’s email systems, file access, and logistics for weeks. After the dust settled on the attack, Mondelez filed an insurance claim for damages, which was promptly denied on the basis that the insurer doesn’t cover damages caused by war. Mondelez’s case remains unresolved.
Merck brought a similar case to court and won. The New Jersey Supreme court ruled that their insurer couldn’t “claim the war exclusion because its language is meant to apply to armed conflict” according to Bloomberg Law. This ruling could “force insurance policies to more clearly confront responsibility for the fallout from nation-state cyberattacks.”
In the meantime, Mondelez has developed a new security awareness initiative to help prevent future cyber-attacks.
Specific actions your IT team can take to prepare
It’s important to note that CISA says that “all organizations—regardless of size—should adopt a heightened posture when it comes to cybersecurity and protecting their most critical assets…Every organization—large and small—must be prepared to respond to disruptive cyber activity.” So, what can you do? CISA has set out a list of recommended actions that you can follow to heighten your cybersecurity posture.
Intrusion Avoidance
Of course, CISA starts by recommending steps to avoid cyber intrusion in the first place. That makes sense, given that intrusion avoidance counteracts the need for all subsequent cybersecurity actions (including post-intrusion forensics, response and containment). With that in mind, here are the five things CISA says you should do now to “reduce the likelihood of a damaging cyber intrusion”:
Validate that all remote access to the organization’s network and privileged or administrative access requires multi-factor authentication.
Ensure that software is up to date, prioritizing updates that address known exploited vulnerabilities identified by CISA.
Confirm that the organization’s IT personnel have disabled all ports and protocols that are not essential for business purposes.
If the organization is using cloud services, ensure that IT personnel have reviewed and implemented strong controls outlined in CISA’s guidance
If your organization is either a critical infrastructure organization (private or public sector) or a Federal, state, local, tribal or territorial government, you can sign up for CISA’s free cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats.
Threat Detection
CISA’s second set of recommendations focus on intrusion threat detection as a way to prevent becoming compromised. Again, the word-for-word CISA recommendations are as follows:
Ensure that cybersecurity/IT personnel are focused on identifying and quickly assessing any unexpected or unusual network behavior. Enable logging in order to better investigate issues or events.
Confirm that the organization's entire network is protected by antivirus/antimalware software and that signatures in these tools are updated.
If working with Ukrainian organizations, take extra care to monitor, inspect, and isolate traffic from those organizations; closely review access controls for that traffic.
Logging is critical to investigating issues and events early. You may be surprised to find that many popular remote access / support solutions lack the ability to provide fast and meaningful log data. Data that specifies who is actually accessing the remote access / support solution, when, from where, for how long, etc. Robust logging among other forms of authorization and auditing can minimize your liability in the event of a hack.
For the complete set of CISA recommendations, including how to prepare an intrusion response and become resilient to a destructive cyber incident, visit CISA's Shields Up page on the Russia-Ukraine crisis.