Zero Trust Simplified
Unified Secure Access Platform with SSE & SASE Services






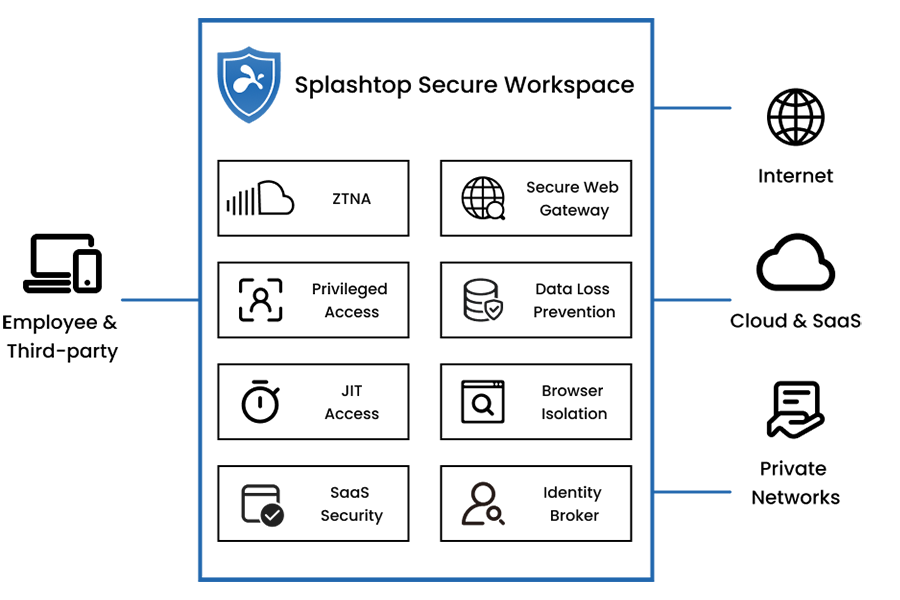
Retire Your VPN and Embrace Next-Gen Zero Trust Network Access (ZTNA)
Enforce zero-trust, default-deny policies for users accessing your internal resources. This approach is faster and safer than a VPN by preventing lateral movement and traffic backhauling.
Secure Third-Party Access with Session Recording and Live Monitoring
Powerful, credential-free, time-bound Just-in-Time (JIT) access with Remote Privileged Access Management (RPAM). Safeguard against internet threats and data loss with Remote Browser Isolation (RBI). Support for BYOD, clientless access, and unmanaged devices, covering both IT and OT environments.
Next-Generation Zero Trust Security
Zero Trust Networking
More secure and faster alternative to legacy VPNs with micro-segmentation, reducing lateral movements.
Least Privileged Access
Zero Trust secure access to only what’s necessary based on identity, role, device, and network context.
Live Session Monitoring
Remote sessions are monitored, controlled, and recorded, complete with full visibility to user activities.
Ease of Use
Ease of Deployment
No more complex VPN policy management. Secure access and connectivity can be set up in minutes.
Just-in-Time Access
Users gain temporary access to resources only when needed, with limited time and precise permissions.
Agentless ZTNA Access
Agentless ZTNA access removes the need for software installation and enable quick onboarding of third-party vendors and BYOD users.

Transforming Secure Access with Splashtop Secure Workspace
Yanlin Wang, VP of Advanced Technology, Explains How to Break the Security Mold to Enable Anytime-Anywhere-Anyone Secure Access to Resources Everywhere

Identity and Access Management Explained: A Complete Guide to IAM
n the rapidly evolving digital landscape, the need to protect sensitive data and manage user access effectively has never been more critical.

How to Mitigate XZ Backdoor Supply Chain Attack
In the digital age, supply chain attacks have emerged as a sophisticated threat vector, exploiting the interconnectedness of modern software ecosystems.

Securing Third-Party Access: Splashtop's Just-In-Time Approach
In the world of IT, the necessity for third-party access is undeniable, yet it introduces cybersecurity risks that cannot be dismissed.






